What’s new and exciting with M365 in June 2024?
Changes to the office 365 Suite
Teams:
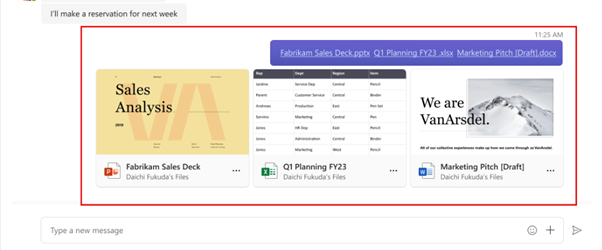
File Preview in Teams:
Microsoft Teams allows you to preview files directly within the app, without opening external applications. Supported file types include:
- Documents: View Word, Excel, PowerPoint, and PDF files.
- Images: Preview common image formats.
- Videos: Play video files without leaving Teams.
Teams Meeting Recordings Changing Location:
Microsoft Teams will in future store meeting recordings in the OneDrive for Business folder of the meeting organiser and not, as previously, in the OneDrive for Business folder of the person who initiated the recording.
New Teams Mute Option for the Windows Taskbar:
In Windows 11, you can mute/unmute your microphone directly from the taskbar during Teams calls.

Use the keyboard shortcut Win+Alt+K or click the microphone icon to control your audio without leaving your work.
OneDrive:
Annotate PDFs Without Leaving OneDrive:
While in OneDrive, you can annotate PDF files:
- Add highlights, and other annotations that can be shared with other individuals.
Sharepoint/Copilot
How Restricted SharePoint Search works with Copilot
Restricted SharePoint Search allows you to disable organisation-wide search, and to restrict both Enterprise Search and Copilot experiences to a curated set of SharePoint sites of your choice. Additionally, whether you have enabled Enterprise Search or Restricted SharePoint Search, users in your organisation will still be able to interact with files and content they own or that they have previously accessed in Copilot.
Restricted SharePoint Search is off by default. If you decide to enable it Copilot and non-Copilot users will be able to find and use content from:
- An allowed list of curated SharePoint sites set up by admins (with up to 100 SharePoint sites), honouring sites’ existing permissions.
- Content from their frequently visited SharePoint sites.
- Users’ OneDrive files, chats, emails, calendars they have access to.
- Files that were shared directly with the users.
- Files that the users viewed, edited, or created.
MAM (Preview) for Windows 365 and Azure Virtual Desktop:
Now in preview, Microsoft Intune Mobile Application Management (MAM) can provide numerous benefits for iOS/iPad OS and Android clients.
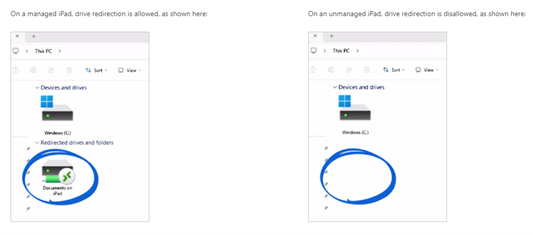
Previously, supporting bring your own device (BYOD) was a challenge because Azure Virtual Desktop and Windows 365 end users had the same redirections whether they connected from a corporate or personal device. For example, it wasn’t possible to allow drive and clipboard redirection on a corporate managed device without allowing the same redirections on a personal device. This posed data loss risk when corporate data was copied to the personal device.
This new feature will allow organisations to configure different redirections when they connect to Azure Virtual Desktop and Windows 365 using the latest versions of the Remote Desktop client (iOS/iPadOS and Android) and the Windows App (iOS/iPadOS) that are integrated with Intune MAM.
There are 4 steps needed to manage redirection using Intune MAM. These steps are mandatory for redirection.
- Intune device filter — This filter allows app configuration and app protection policies to be targeted for specific devices, regardless of whether they are enrolled or unenrolled.
- Intune app configuration policies help manage redirection settings for the Windows App and the Remote Desktop app on a client device.
- Intune app protection policies – Specify the security requirements that must be met by the application and the client device. Use filters to target users based on specific criteria.
- Conditional Access policies – Control access to Azure Virtual Desktop and Windows 365 and ensure criteria set in app configuration policies and app protection policies are met.
The screenshots below illustrate the key steps to configure different redirections on personal devices. For this example, we will disable drive redirection on a personal iPad so corporate data cannot be copied to the local iPad storage.
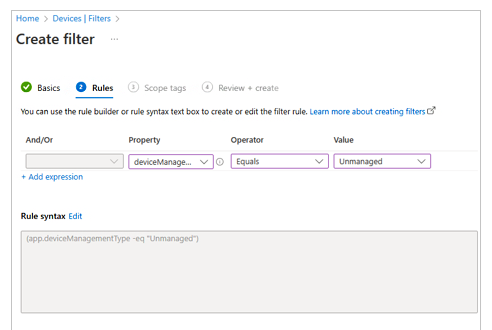
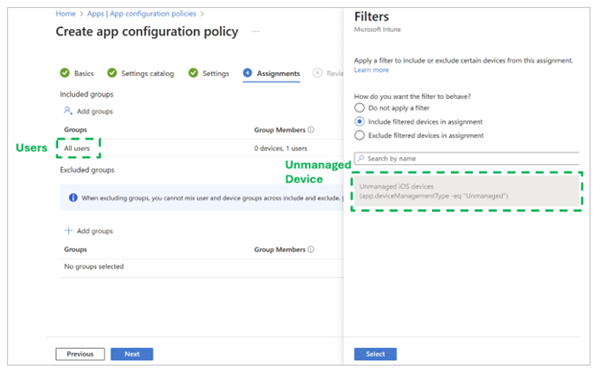
- Create a filter for unmanaged devices.
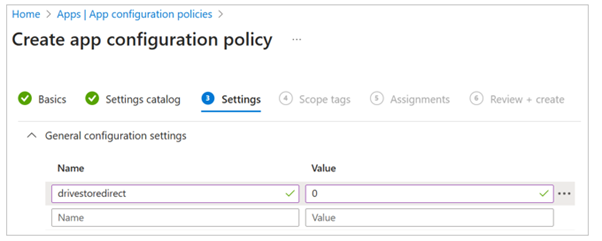
2. Create an app configuration policy to disable drive redirection using the Remote Desktop Protocol (RDP) property name of drivestoredirect as listed in Configure device redirection. Assign a value of 0.
3. Select the groups the Intune app configuration policy applies to (hence the groups the redirection settings apply to). Select Edit Filter and choose the unmanaged devices filter that was created earlier.
4. Sign in to your Azure Virtual Desktop session host or Windows 365 Cloud PC.
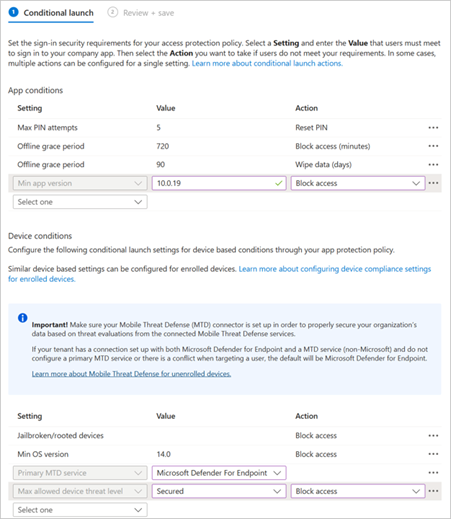
In addition to different redirections, you may also want to require a minimum OS and Remote Desktop app version to reduce the risk of threats caused by older and potentially unsupported devices that are not current with the latest security updates. Configure an Intune app protection policy to do this. In the example below, you can require that the Android device be:
- Android 14.0 or later.
- Remote Desktop 10.0.19 or later.
- Determined as Secured – no threats – by Microsoft Defender for Endpoint.
Without managing the personal device, Intune MAM allows you to:
- Disable specific redirections on personal devices.
- Require PIN access to app before connection.
- Block third-party keyboards.
- Specify a minimum device operating system version before connection.
- Specify a minimum Windows App and/or Remote Desktop app version number before connection.
- Block jailbroken/rooted devices from connection.
- Require a mobile threat defense solution on devices, with no threats detected before connection.
Windows 11 Config Refresh:
In general settings are evaluated during Intune check-in which happen around every 8 or so hours, and require the device to have Internet connection, so devices that currently appear offline have no real way of checking setting that have been changed by a user/admin/or threat.
This is where Config Refresh come into play and will re-evaluate the current configuration and revert any changes that have been made back to required state even if the device is offline.
Some of the key new features are:
- A reset operation to reset any settings you manage which use the Policy CSP
- Configuration options to allow reset of managed settings to take place as frequently as every 30 minutes
- Offline functionality, not requiring connectivity to an MDM server
- Ability to pause Config Refresh for troubleshooting purposes with automatic resume after 24 hours
*To enable Config Refresh, your PCs must be running Windows 11, version 23H2 or version 22H2 with the June 2024 security update installed
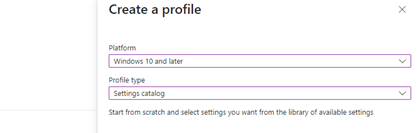
In Order to setup Config Reset follow the below steps:
- Create a Device Configuration Profile and select Settings catalogue as the profile type
2. Under the settings picker search for “Config Refresh” and then select “Config Refresh” and “Refresh Cadence”
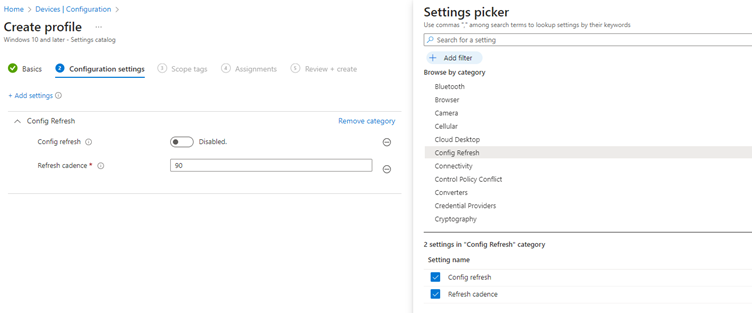
3. Set Config Refresh to Enabled and then enter the duration under cadence (This is in minutes)
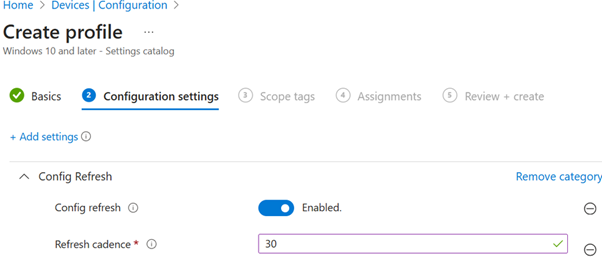
Important: Config Refresh is designed to work with MDM policies managed by the Policy CSP. Some policies, notably the BitLocker CSP, will also adhere to Config Refresh enablement. Other policies are outside of this scope, such as Firewall, AppLocker, PDE, and LAPS.
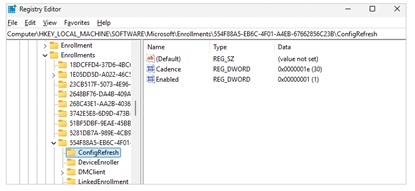
Once the Profile has rolled out you will be able to find the new entry in the Registery Editor and it will contain two values “Cadence” and “Enabled”
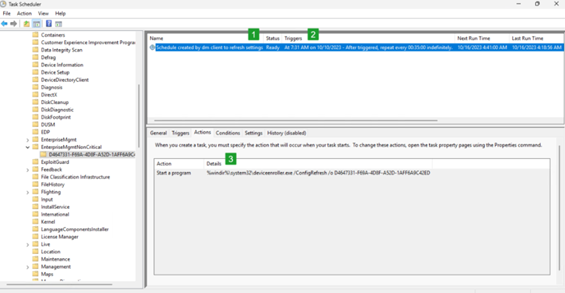
The way that this is all works is by the creation of a new scheduled task found at: Task scheduler library -> Microsoft -> Windows -> EnterpriseMgmtNonCritical -> Intune policy provider GUID -> Schedule created by dm client to refresh settings
There might also be a case for pausing the config refresh and this is where the last setting: PausePeriod can come in Handy. This process used to be fairly tedius by editing your current CSP policy however Microsoft have now added “PausePeriod” to device actions in Intune.
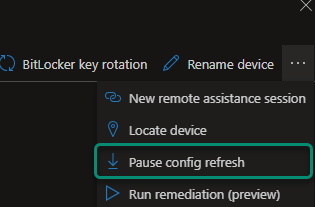
Which will allow us to Pause Config Refresh from Between 0-1440(24 hours) minutes.
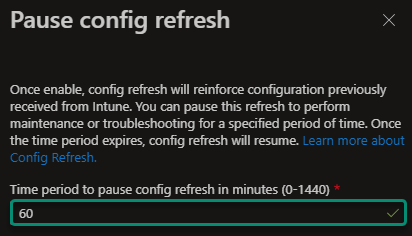
And Finally
If you want to know any more about anything Microsoft or Azure then please feel free to reach out to us by giving us a call of dropping us an email.
01789636799





